Security should be a priority for any business, to be aware of the potential security vulnerabilities and protect your Salesforce data.
What steps can you put in place to improve Salesforce security? We’ve outlined how you can check for Salesforce security vulnerabilities, as well as some best practices to help protect you against cybercriminals.
Cyberattacks are a constant threat. The last year has seen a dramatic increase in companies’ reliance on technology as many teams began working remotely. In fact, data breaches exposed 36 billion records in only the first half of 2020, which was twice the amount in all of 2019. This trend is unfortunately forecasted to continue.
Salesforce Health Check Scan
Your Salesforce system allows for a series of security settings that can be adjusted to best fit the needs of your company. However, improperly configured settings leave your system vulnerable to attacks.
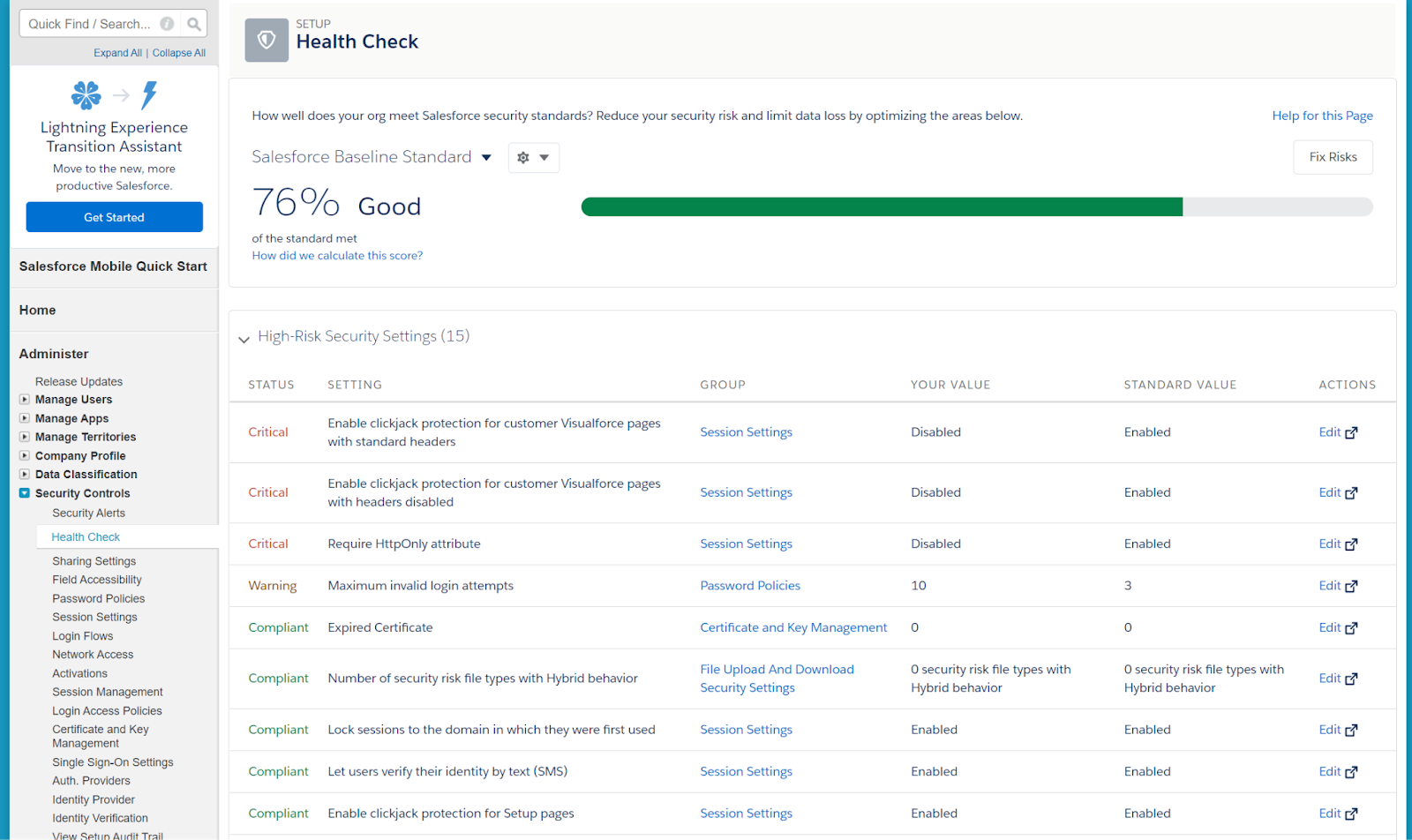
The Salesforce Health Check scans your system to identify and fix potential security issues created by improper settings. Your system will be compared to a baseline standard and given a score based on adherence to recommended practices.
This standard can be adjusted to best fit your needs, as Salesforce is used for many purposes and in multiple different industries with different requirements.
Simply navigate to Setup and enter Health Check in the search bar. You can also select Health Check on the Administration Setup page as well. Select your intended baseline and let the system work its magic.
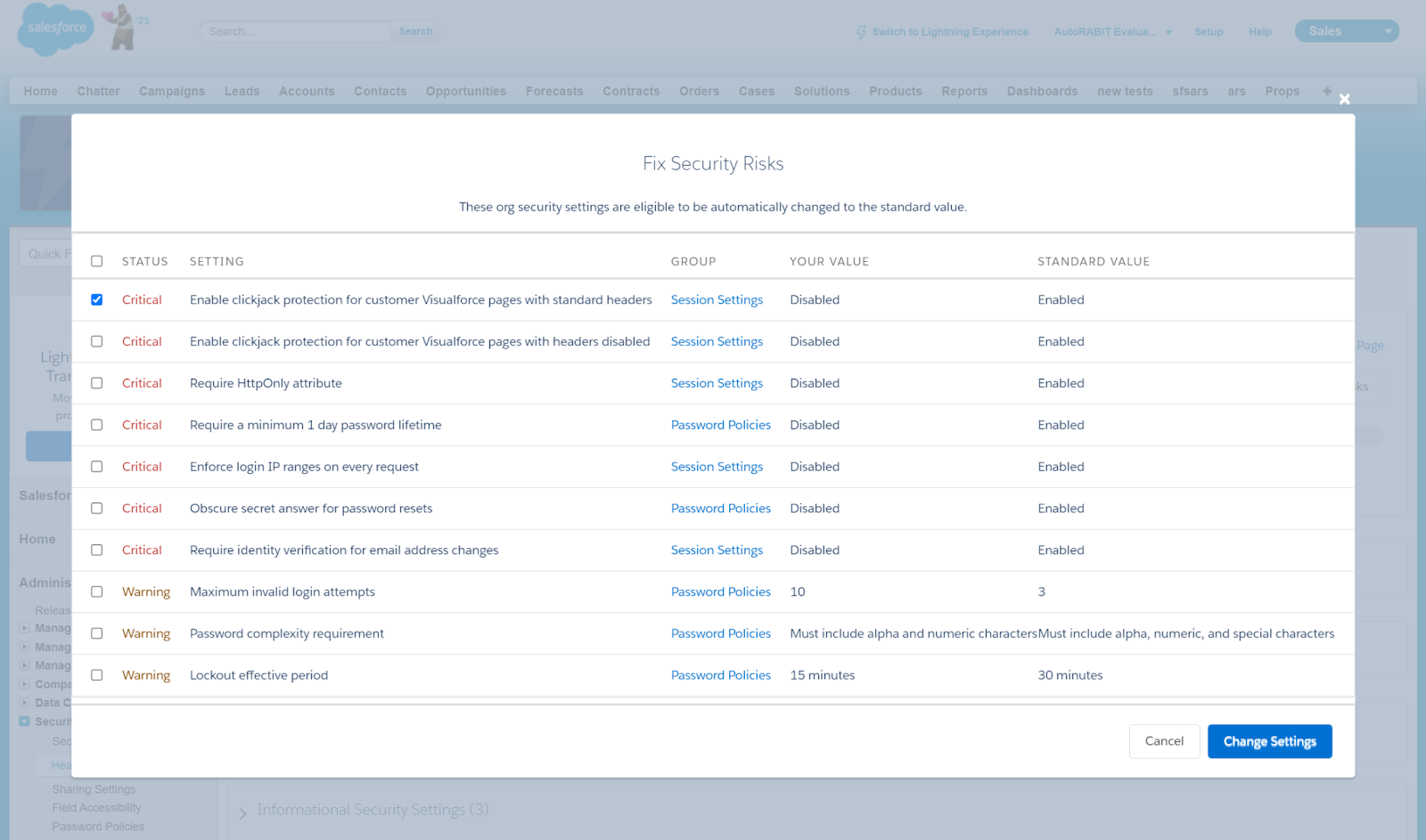
You’ll see a percentage score on top as well as itemized suggestions to increase your level of security. Clicking Fix Risks will quickly reconfigure the recommended settings.
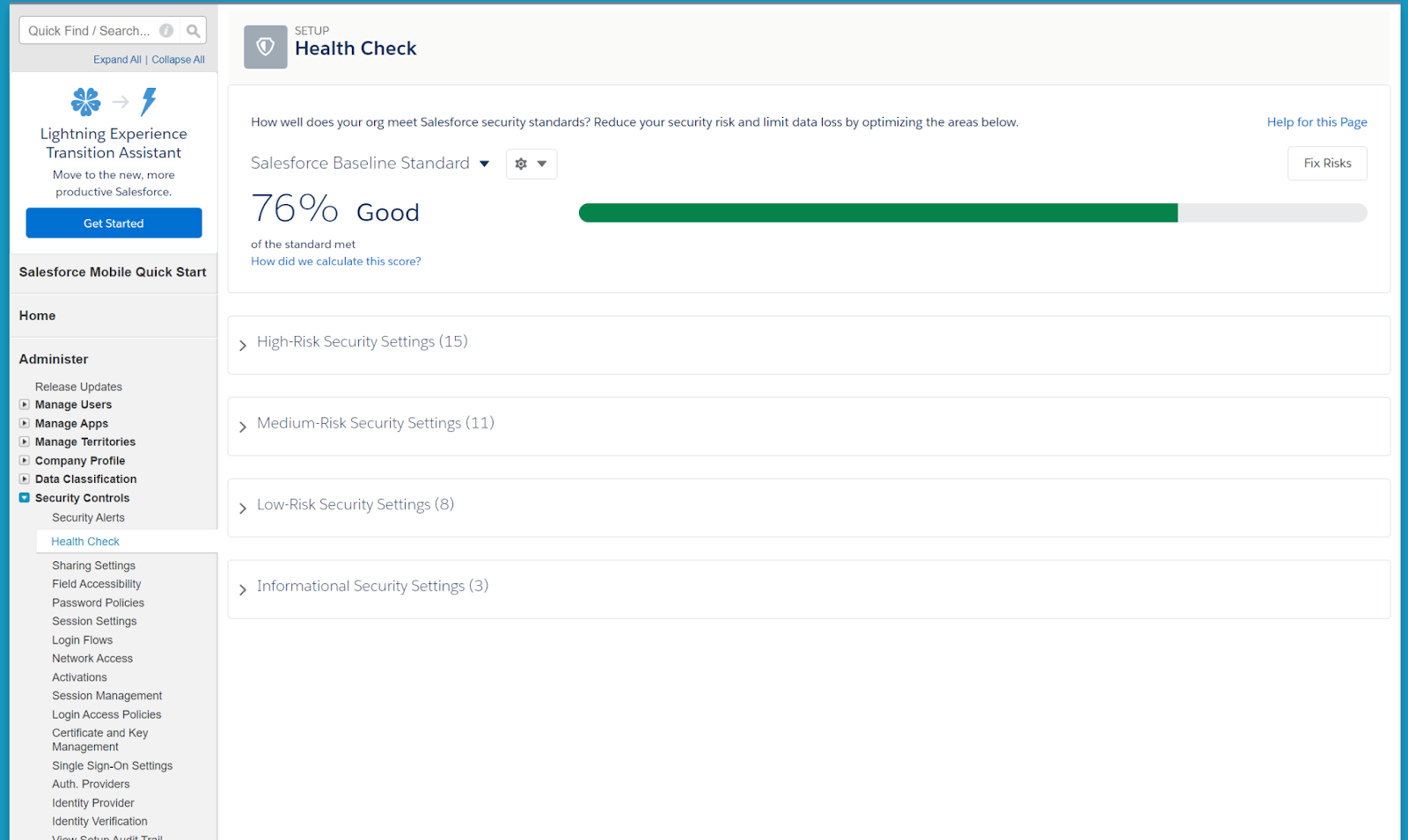
Your percentage score alerts you to the seriousness of the issues found—higher numbers signify greater risks. These risks will be separated into categories depending on their seriousness: High-Risk, Medium-Risk, and Low-Risk.
This will help you prioritize your actions and point you toward vulnerabilities to address moving forward. The security risks will be listed so you are aware of all potential hazards.
System Audit
One of the biggest advantages of Salesforce is that it can be used for a variety of tasks. However, the breadth of the system also creates potential security vulnerabilities.
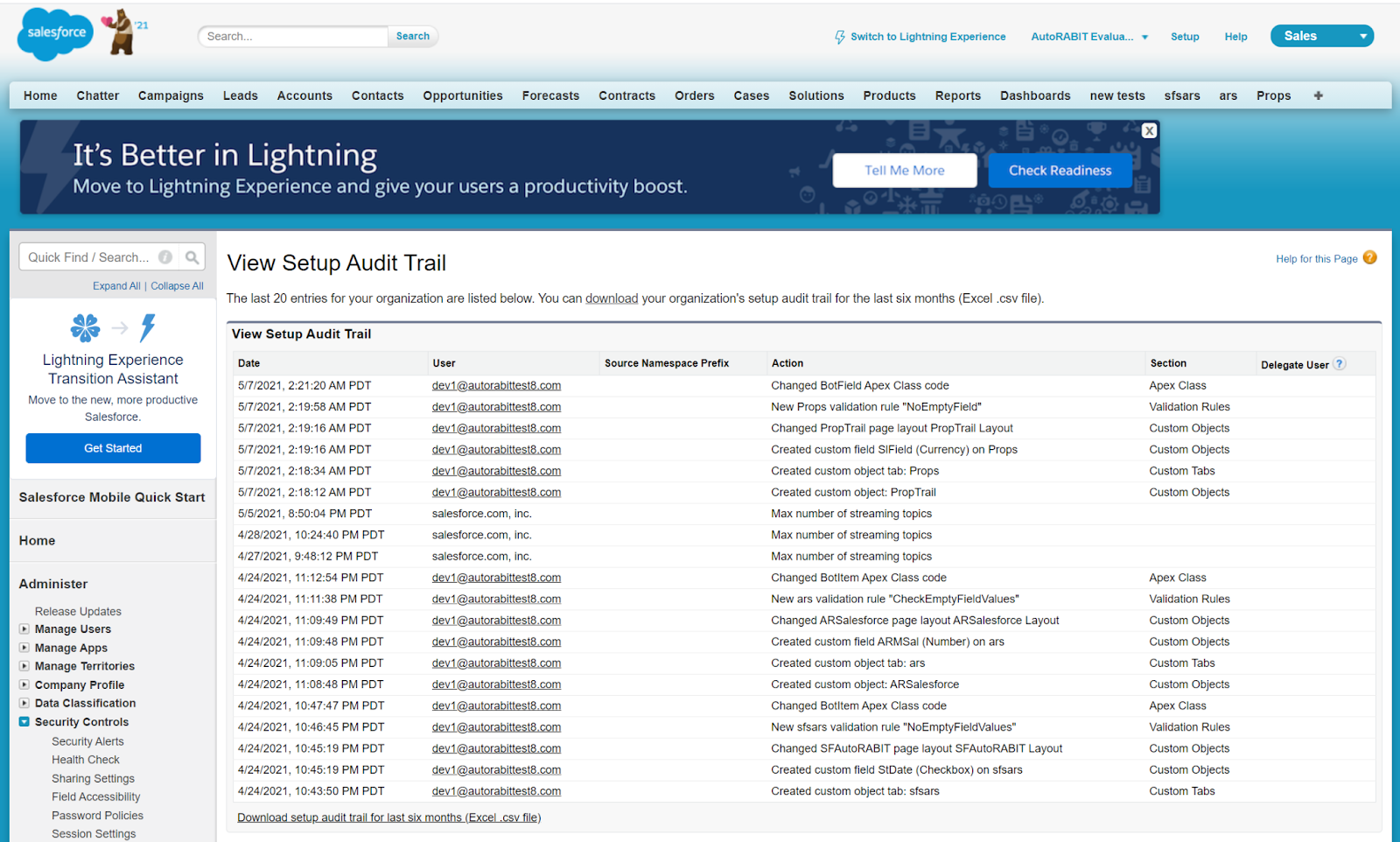
Salesforce offers the ability to audit your system to find any security issues that might have slipped past your attention. These reports can be used to locate potential issues which can then be addressed on a case-by-case basis.
Inspect the results of these audits for any unauthorized or unexpected changes or statistics.
Audits can be used to check:
Record Modification Fields
Keep track of who created the record as well as who last edited the record.
Login History
Any unauthorized attempts to access your system will be present in the complete login history—this includes all successful and failed attempts.
Field History Tracking
Perhaps you have specific fields that are more sensitive than others. These individual fields can be monitored to track value changes.
Modifications to Organization Configurations
Visibility into system changes provide administrators an updated overview of their Salesforce environment. Audits can be implemented to track these changes.
Security Best Practices
Set User Permissions
Unrestricted access to Salesforce repositories creates overexposed data. Set user permissions so team members can’t access more information than they need to perform their duties. User permissions can be defined by values such as object visibility, field visibility, and record access.
Backup Data Frequently and Plan for Recovery
Cyberattacks aren’t the only way a company’s Salesforce data can become lost or corrupted—accidental deletions are unfortunately common. A reliable and scalable backup and recovery tool built specifically for Salesforce protects you from losing functionality and enduring redundant work to get back to baseline.
Data Segregation
Cybercriminals can exploit a variety of potential entry points. They will then attempt to access as much of your system as possible once they’re inside. Segregating the various sections of your Salesforce platform will contain the breach to a singular area instead of compromising your entire system. Instituting access measures between various sections make it more difficult for cybercriminals to move throughout your system.
Barriers can either be from utilizing different firewalls, physical connections with different wiring, or separating them virtually. Find out more here.
Educate Employees About Phishing, Malware, and Password Protection
95% of breaches are due to human error. Education is the best way to combat this possibility. Train your team members to spot phishing and malware attempts through their company-issued email addresses, as these are still two of the most popular methods to gain access to your system.
Teach your employees to protect their login information by avoiding these threats while also utilizing strong passwords.
Summary – Remain Vigilant
Data security should be a constant effort. Technology and tactics will evolve—your security efforts need to evolve along with them. Continually monitoring your Salesforce system for potential vulnerabilities and addressing them will give you the best chance of avoiding a data disaster.